
What are the advantages of SIEM?
Since security incident and event management (SIEM) offers obvious advantages, it has been widely embraced and utilised to manage cybersecurity events. As a result of the growing need for cybersecurity automation, the SIEM industry is anticipated to rise by around 25% over the next five years. Despite the market's growth, SIEM costs have mostly remained stable.
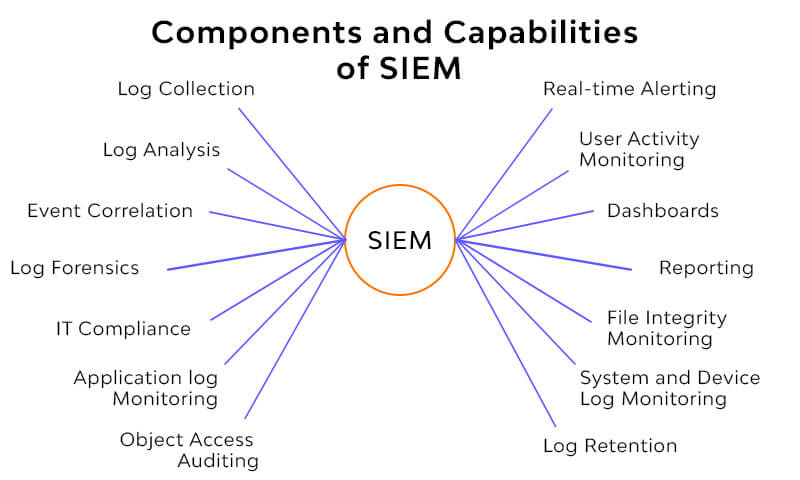
SIEM is the practice of continuously logging, tracking, correlating, and analysing security events in an IT system. SIEM tools can be quite helpful for anything from compliance reporting to thwarting cyberattacks, regardless of the size of a company. The addition of SIEM software to a managed services provider's (MSP) product line can be advantageous.
SIEM tools combine the capabilities of security event management (SEM) and security information management (SIM). They enable proactive rather than reactive cybersecurity by using log data flows from many organisational departments to build a real-time picture of potential threats to the IT environment.
SIEM systems can provide you a comprehensive understanding of what is happening at every level of an organisation by relying on data from the various hosts in an IT environment.
The advantage of SIEM to your organisation
Rapid and efficient SecOps
Using analysis templates to quickly examine log and threat intelligence data, SOC analysts may quickly get a hold on what's going on with a SIEM digging through millions of data points. This can help both in responding to a security threat and the negative effects of a cyberattack.
Without a SIEM, security analysts would have to manually decipher the many security device logs and data sources, like threat intelligence feeds. It greatly slows down incident response in addition to burning out personnel, which is a major issue in and of itself.
By setting up your SIEM solution to react to incidents in real-time, you might potentially prevent data loss or worse for your business.
Increased Security Alerting and Threat Detection Accuracy
Individual security data streams would not be able to detect and identify threats as effectively as SIEM technologies can using their huge data sets. They can also add valuable context to issue alerts and improve security event data.
With cyberattacks becoming more sophisticated, they can avoid detection better than ever. SIEM tools can identify the different elements of attacks on different hosts on a system by gathering and normalising log data from different systems.
As an example, a computer's operating system might see one part of an attack, while a network intrusion prevention system might see another. A tool that correlates log information from each host determines the nature of the attack and whether it was successful by reconstructing the series of events.
Data centralisation
SIEMs gather security data, enhancing its capacity for analysis and application in processes for responding to incidents. Additionally, this may lead to greater enterprise-wide security landscape visibility. The SIEM often normalises security as well. The many data streams entering the SIEM have various schemas and fields in their unprocessed state. It's not accepted as usual.
For instance, information about users that comes from network logs, email servers, databases, and mobile devices may all take different formats. This is a challenge for event correlation and data processing. The data can be restructured by the SIEM to make it uniform for incident analyst and response procedures.
Another advantage is data storage. For more extensive analytics and reporting, the SIEM can store normalised security data. This also helps with compliance.
Simplified compliance reporting
Almost every company, regardless of its size or industry, has at least some regulations that it must follow. Making sure you are adhering to those regulations and demonstrating compliance can be time-consuming and challenging. By gathering, normalising, and organising log data, SIEM technologies can streamline the compliance reporting process. Some firms use SIEM systems as a primary compliance reporting solution due to their advantages as centralised logging solutions.
Most IT environments require complete, customised reports that include all significant security events logged across all hosts to meet reporting requirements. Without a SIEM solution, you are unlikely to have dependable centralised logging capabilities.
This means that you may need to manually retrieve data from each host in your IT system, or you may need to build individual reports for each host and then combine them to make a single report.
This is especially difficult since, in the absence of SIEM systems that automatically normalise your log data, each host in your system is likely to report its data differently, making correlation a time-consuming procedure.
SIEM systems can save organisations both time and money by streamlining compliance reporting and ensuring that MSP customers are not in violation of any rules. Businesses may face substantial fines and loss of accreditation if they do not provide accurate data to demonstrate compliance.
MSPs can readily generate reports using SIEM systems that detail their customers' compliance with the relevant regulatory requirements.
Greater Network Visibility
Network overviews are made simpler by SIEM log handling and aggregation. In fact, "black spaces" can easily exist in a network due to the complexity and diversity of modern networks. As a result, network management and security teams become less aware of what is happening with databases, servers, devices, and third parties as the network grows.
On networks, hackers search for unlit areas. It allows them a space to evade detection while moving laterally across digital assets and disguising persistent threats. By gathering security event data from throughout the network, SIEM reduces this risk. It then stores it centrally and conducts analysis on it. These "black regions" can be illuminated via SIEM log analysis.
In a nutshell, the integration of SIEMs into a SOC could be quite beneficial. They combine security data feeds, allowing them to identify significant security problems and take appropriate action before they become too late. After that, they help the SOC team respond quickly and effectively.
Simultaneously, setting up and fine-tuning the alerts and replies in SIEM software might take a lot of time. A considerable time and resource commitment on the part of the security team is required to start a SIEM project. Aiming to achieve long-term success, it should be carried out with careful planning and a reasonable budget.
Get in Touch.
Let’s discuss how we can help with your cloud journey. Our experts are standing by to talk about your migration, modernisation, development and skills challenges.




