
Who is your sysadmin at Home?
Let’s get the clickbait out of the way, the answer is You! and now the why and how and the rest of the story.
Working from home isn’t a new concept, specially after a major pandemic, but we are still learning from it even today.
While EDR and MDM and VPN and other TLA, does help to protect company assets and at some level help to protect the employee too, there are few things which you can (and should?!) do in your own network, where the corporate IT usually can’t help.
I will guide you thought my top 3, and break them down, what is the risk, how to mitigate it, why is it important and how the pro’s do it.
To give you the nutshell version before you commit reading thought a long, detailed, technical and often sidetracked whole story here is the super short list:
- Choose your DNS server right
- Don’t relay on defaults
- Keep up-to-date every device in your network, yes the fridge, light switch, robot hoover, router, AP counts too
1. Name resolution
What is the risk?
When you enter a website to your browser, or your mail client reach out to the an IMAP server, or your IM connects to your workplace, or just simple the VPN dials in, the story starts with a name resolution, you need to translate between the (mostly) human readable domain name and an IP address. This is a crucial step as while DNS cache poisoning and other DNS attacks are not frequent, the effects are sever and devastating.
While most communications are nowadays encrypted and domain hijack could be detected by the client side application, by either certificate pinning, or even just as a first step chain validation, in better cases including CAA records for the domain, there is still a risk, specially if humans are involved, as way too many people learned how to “just click accept” on a certificate warning, hence we should do what we can to avoid it.
How to mitigate it?
First and foremost pick the right DNS server, this sounds at the same time trivial and complicated so let’s dive in, what makes a DNS server good and what makes it bad.
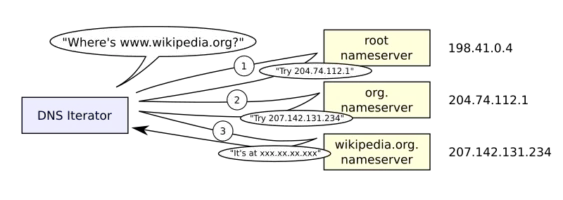
Since TTFB, is pretty important for SEO and any UX highly depends on speed, you can’t wait around for name resolution, hence back in the old times ISP’s started to build out their own DNS servers, because within the TTL of the response the query could be answered right away from cache, hence the customer was happy, but running a DNS server is not just non-trivial, it’s also a huge responsibility, apart from the security risk involved (see for example DNS reflection and amplification attacks), if there is no name resolution, “there is no internet” or as nowadays their would say “there is no WiFi”. In parallel to ISP’s efforts, large organizations started to create public DNS servers like Google in 2009, and till today it’s one of the biggest public DNS server service, next to giants like Cloudflare or Cisco (OpenDNS) or even specialists like Quad9 or AdGuard. These become popular at the time when ISP DNS fault was a common source for outage, and they still stand strong today, and frankly they are one of the good option, although I can not recommend all public servers, but to avoid the sidetrack I will leave that subject for the next article.
But so far we only clarified that you want something quick, and the fact that you have options, but how about the security aspect. How can a DNS server be more secure (from client point of view) then an other DNS server?
- Privacy
- Validation
- Filtering
Let’s start with privacy as that’s a funny one. For an entirely different reason, few years back , VPN providers popped up every corner offering no logging, privacy enhancing services, and one of the frequently highlighted claim is that their protect you against your ISP seeing what sites you visit and sell of that data for marketing purposes. This is mainly based on DNS data as while DNS is well maintained, reverse DNS isn’t, and even if would be, with CDN’s with SNI’s you still would have a large percentage of hit and miss. In a nutshell there is a general concern around having your DNS traffic intercepted, and monitored, and to be fair considering the fact that DNS is by default non encrypted, isn’t far fetched. Here comes to the picture the encrypted DNS protocols, and I say protocols, because there are a few and will be a few for the foreseeable future as if consensus wasn’t achieved yet, it’s unlikely that it will happen quickly (I am rooting for DoH , but who knows, maybe with the popularity gain of HTTP3 DoQ will win this one)
Not going too deep into the full list of options, and it’s benefits and downsides as it’s again outside of the scope of this article, so just highlighting that a good choice of upstream DNS server supports at least one of the encrypted protocol (DoT, DoH, DoQ, DNSCrypt) so what you are looking for stays between you and the DNS server provider, not for everyone between.
Second and actually more important aspect in choosing your upstream DNS server setup is validation. While there are very little penetration of the DNSSec as a protocol (at least for my taste it ‘s low), it would offers an option to confirm the validity of the DNS response. This is where the client can be smart about it, and MDM makes a difference. With DNSSec validation turned on invalid responses are just ignored by the client, however it’s even better if it does not even make it up till your network, just in case one of the client isn’t set up right. The basic idea is that the DNS servers digitally sign the domains and the client validate that signature. This is why I wanted to add to Lynis too, but I just noticed that it’s still disabled.
Privacy, Validation out of the way let’s see the last aspect which is Filtering.
This is a controversial subject, but I will try to cover both ends of the arguments. When you ask for a domain name resolution, a whole chain of servers are involved, most of the cases you have name resolution on your client itself (host files at least) then you have a local DNS server on your router, then a chain of upstream servers, and it ends with the domain owners server, at least the first time around presuming normal operation, however any of the servers can decide to lie to you, or just refuse to answer.
At least in some cases, in some countries, this is enforced by local laws which mandate ISP’s to redirect certain traffic both on IP route (via non validated BGP announcement from the governments DPI) and from DNS point of view too. Typically these state controlled intercepts are for domains which in they eye of the law doing something nasty, for example running a gambling site without paying the local taxes, offering access to non licensed media content, or otherwise associated with illegal activity. Obliviously this is a slippery slope as once the technical, and legal capabilities are built within a country to step in and limit the internet access, there is very little guardrails to prevent abuse of systems like this, but let’s leave that unsettling thought for an other day and just accept that filtering exist even on a “mandatory bases”. Then you have other filters which the users are looking for, for example, known scam sites, malware controller domains, advertisement, user tracking, marketing agencies, adult content, and many others which might be as a whole category is unwanted by the network owner. These filters can be either configured in some cases (for example OpenDNS Home or AdGuard) or just set for you based on which server you pick. For advance users you can of course run your own server with as much customization as you please, popular options here are Pi-hole and AdGuard home.
As you can see in filtering the options list is long and there is no clear winner, if you either have every “home-work” or have less freedom, or no filtering at all, so it’s really personal preference, but you should choose, and this nicely lead to my next big subject of defaults.
2. Defaults
What’s the risk?
When you order a new internet connection, buy a new laptop, install a smart light etc etc, it comes with all kind of defaults, most of with is there to easy the user adaptation, to make the user experience smooth. In the recent years we made a huge leap in having these defaults more secure, but we are still far away from actually secure.
Case in point there is even a dedicated website just for default router passwords which is accessible the same way for you then it’s accessible for an adversary, even if that’s just a spay attack like when they hijacked DNS setting on local routers via single pixles embedded in html e-mails.
Chaining the default, should be the default, but it’s not so let’s acknowledge why there are still so many devices out there with default password, default SSID names, default UPnP settings, default WPS state and many more. Two main reason and only one has an easy fix, the first is that we forget things, and that’s easy to fix, just record it, ideally in some secure storage like your password manager, but let’s be honest writing your IP range on the back of your router sitting behind some pot of flower on an inaccessible shelf, isn’t a crime which Security people will hang you for. The other reason why we have so many defaults is the lack of care and awareness, this is much harder nut to crack but one of the aim of this blog post is to address this so let’s hope once you read it, you will share, and so on.
To underline my point, here is an example where defaults where just not good enough, even thought you wouldn’t think of it first.
The first bunch of WiFi routers started with default passwords, for the admin interface and a default password for the network access too (or some cases maybe even no password) as the idea of “don’t use defaults” isn’t something I come up with, manufacturers started to twist things up and started to use semi random credentials for both administrations and network connection, but to be able to provide support to the enduser even if their peal off the password sticker from the device, they have to be able to either reproduce it, or store it, and this unnamed ISP choose the first option. The trouble was that they used only publicly accessible data for the password generating function, so based on the SSID and the MAC address of the wireless interface, you could generate the password, aka PSK for the network, which did not stay secret for long, and suddenly a bunch of home network just become practically “open”, and the fact that both the SSID and the password looked like random, looked secure, just made it worst, as it remained the default for more, as it looked OK already.
So review and update your defaults, in case of a router I would suggest to change if possible: DHCP range, admin user, admin password, wifi SSID, Wifi key, UPnP off, WPS off, Cloud management off, automatic firmware update on.
How to mitigate it?
There is no magic sauce for this, simply when you add a new device, just review those settings, walk thought the options, and change at least the passwords if nothing else. There are plenty of good write up about home router setups, just be curious and that should be enough to get you started.
And worth noting many of the ISP nowadays provide pretty locked down firmware with their devices, so if you don’t want to push it to the point of getting a different router, or even just to flush a new firmware, then the options which you can actually change is likely to be a short one, so don’t be scared to poke around.
3. Update, update, update
What is the risk?
The importance of upgrade is pretty well discussed subject, how vulnerabilities and weaknesses are used to take over systems, cause harm or at least inconveniences, but the scope is often overlooked, and limited to only mobile devices, and pc’s and other more visible devices. The reality is that we are in the age where everything is getting smart, from home appliances like fridges or dishwasher, across small electrical things like egg trays, and robot cleaners and sex toys, all the way to the biggest tractors and cars even massive crane’s lubrication systems, everything is getting smart. Which is most of the time also means internet connection, although at least with OSS movements like the Home Assistant (massive shout out to the guys) manufacturers starting to understand that WiFi connected ≠ Internet Connected, Smart ≠ IoT, and Connected ≠ Works only connected.
But still a large percentage of devices will act just like any other node on your network, visit websites, upload data, download software etc etc, yet we rarely think about installing an Antivirus on your dishwasher, or run a malware scan on your light switch. I hope you are now already wondering the how you can protect “the rest of the network”, so let’s jump in.
How to mitigate it?
First step is the inventory, it’s trivial that you can’t protect something is you don’t know about it, pretty much the sales pitch of runzero in a nutshell, but it’s true so let’s start there.
You can start just with a simple pen and paper and walk around the room, you might be surprised how many times this will already reveal a bunch of devices you haven’t updated recently, or maybe even never. But once that’s done, it’s time to go deeper and find the things out of sight too. A good place to look is the choke point, which is the router of the network, you will have a DHCP server running on the router itself, at least 99.99% of the time, not covering here the static IP allocated networks nor 802.1X, where you obviously already have a better more accurate inventory then what DHCP can give you. So if you see a device on your network, you have a good chance that you can guess what it is based on it’s MAC address and some OUI lookup, if you are brave enough to go against the wild kids or non-techie significant other you can ensure that the DHCP server only provides addresses to know MAC addresses, and that way you will not forget to update your inventory when you get a new device, just watch out that new privacy features specially in mobile devices like to random generate MAC’s now, so at least for your home network you will have to disable that randomness.
Now with an inventory in your hand you can start to review the update methods, can the device self update, is the self update on, do you have any option to request the current version, do you have something to monitor it with, where does the vendor or the maintainer publish about new versions, and once you have all of this, then you can plan your updates for everything!
Have fun running your home network! :)
Closing words:
I hope you learned something from this post, I had fun writing it, there is way more where this come from, I am running my home network in enterprise level, with IDS and SD-WAN and VLAN’s and port security and etc etc, so if you want more, clap, share, comment, or just drop me a message.
Get in Touch.
Let’s discuss how we can help with your cloud journey. Our experts are standing by to talk about your migration, modernisation, development and skills challenges.
