AWS Private Marketplace setup for organisations
29 August 2023
In today’s fast-paced and dynamic business landscape, cloud computing has become an indispensable tool for organisations seeking to enhance their agility, scalability, and efficiency. Amazon Web Services (AWS) has emerged as a leading cloud provider, offering a wide range of services to meet diverse business needs.
Part of the AWS ecosystem is its Marketplace — online software store that helps customers find, buy, and immediately start using the software and services that run on AWS.
However, as organisations embrace cloud services, they also need to ensure that their operations adhere to stringent compliance regulations and security standards. Out of the box usage of AWS Markeplace can result in shadow IT, not following the organisations purchasing guidelines and can even lead to breaking the law by not following accounting standards.
This is where AWS Private Marketplace steps in, providing a comprehensive solution for managing purchases made within the organisation.
Understanding AWS Private Marketplace
AWS Private Marketplace is a feature designed to help organisations streamline their cloud adoption while maintaining strict control over the procurement and deployment of AWS services. It acts as a curated catalog of approved AWS products, services, and solutions, accessible only to users within the organisation. This approach allows businesses to define a pre-approved set of resources that meet compliance and security requirements, thereby minimising the risk of unauthorised or non-compliant deployments.
Key Benefits for Compliance Management
- Controlled Procurement: AWS Private Marketplace enables organisations to create a customised marketplace of AWS products and services that align with their compliance needs. This ensures that only vetted and approved resources are available for procurement, reducing the possibility of unintentional violations of compliance standards.
- Regulatory Alignment: Various industries are subject to specific regulations and standards, such as GDPR, HIPAA, PCI DSS, and more. AWS Private Marketplace enables organisations to pre-select solutions that have already undergone rigorous compliance assessments and align with these industry-specific regulations. This minimises the effort required to demonstrate compliance during audits.
- Centralised Governance: With AWS Private Marketplace, organisations can centralise the management of their cloud resources. Admins have the authority to review, approve, and manage which AWS services are available in the marketplace, ensuring that only compliant and secure options are accessible to users.
- Enhanced Security: Compliance often goes hand-in-hand with security. AWS Private Marketplace helps organisations mitigate security risks by offering a controlled environment for provisioning resources. This reduces the potential attack surface and limits the exposure of sensitive data, contributing to overall compliance efforts.
- Consistent Workflows: Standardising the procurement and deployment of AWS services through a private marketplace ensures that all users follow consistent workflows. This reduces the chances of human error and makes it easier to enforce compliance policies throughout the organisation.
- Simplified Auditing: Compliance audits can be time-consuming and complex. AWS Private Marketplace provides a centralised view of all approved resources, making it easier to demonstrate compliance to auditors. The ability to showcase a curated selection of services can expedite the auditing process and lead to better audit outcomes.
- Scalability and Growth: As organisations grow, managing compliance becomes more challenging. AWS Private Marketplace scales with the organisation, accommodating changes in requirements and ensuring that new cloud resources adhere to established compliance guidelines.
So to summarise:
- Looking from the customer end user side AWS Private Marketplace (PMP) controls which products, users in your AWS accounts can procure from AWS Marketplace.
- It is built on top of AWS Marketplace
- It allows central teams (CCoE) to create curated lists of products to be used in the organisation (and deny any other products)
- Private Marketplace is shared across the organisation, but can be customised with Experiences for specific accounts
- Private Marketplace can integrate with 3rd party procurement systems to fit into existing processes
It can help organisations to manage their compliance challenges :
- Prevent unauthorised purchases via AWS (shadow IT)
- Meet regulatory guidelines for accounting standards (eg related to upfront payments)
- Manage procurement processes centrally (unapproved contractual relationships)
- Control a curated list of approved software (unapproved service purchases)
- Missing auditability
Setup of the service
At this point in time the AWS Private Marketplace setup cannot be delegated like for example GuardDuty or Systems Manager. We can however use existing AWS Organisations features in order to achieve a similar and still manageable setup.
Below picture outlines a possible design for AWS Private Marketplace deployment inside an AWS organisation:
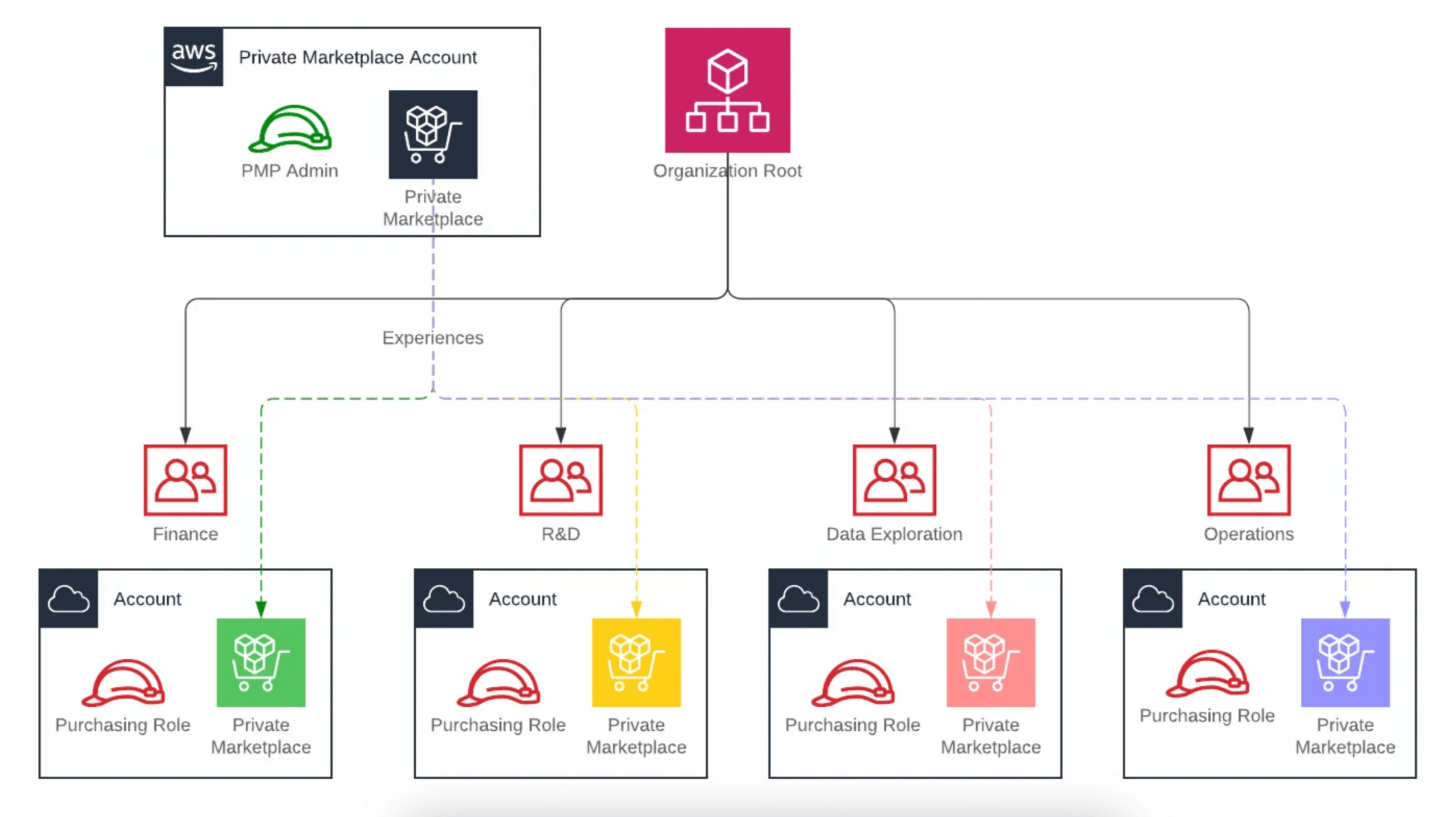
Main points of the setup:
- Private Marketplace Account : This is the designated account that will be used to manage the Private Marketplace inside the organisation to curate the product lists and manage requests. Usually this would be owned either by the Procurement/Accounting team but other options like the FinOps or the CCoE/Central Team are also feasible. Because at the time of writing this article, there is no possibility to delegate this setup, a similar functionality will need to be deployed via the use of SCPs (more on that later)
- PMP Admin: This is the designated role that the Procurement team will assume to perform their duties while managing the Products.
- Purchasing Role: This is a role deployed to all of the Member accounts. We will use this role to make the actual purchases on the Marketplace. While not strictly needed, having this role can help with auditability. Organisations can build their own automation to allow its end users to assume this role after a request is made. Currently AWS Private Marketplace does not offer central reporting features so having such a role and process on top, can help track who is purchasing what
- Experiences : These represent different curated product catalogues that can be made available to different groups within the organisation (here it’s Finance, R&D, Data Exploration and Operations). Different colors in the picture show different experiences attached to different account types. Currently AWS doesn’t allow us to assign Experiences via OU’s so if your organisation decides to go this path, the assignments will need to be made on an account basis. If your organisation chooses just to have 1 common experience, this can be assigned to all current and future accounts using the root ID of the organisation.
The PMP admin role is limited in its permissions to managing the Marketplace and on top of that has read only access to the PMP Account. The CloudFormation code can be found below:
---
AWSTemplateFormatVersion: '2010-09-09'
Description: >
Creates Marketplace PMPAdmin IAM roles for deployment in PMP account
Resources:
MarketplaceAdminRole:
Type: 'AWS::IAM::Role'
Properties:
RoleName: PMPAdmin
AssumeRolePolicyDocument:
Version: '2012-10-17'
Statement:
- Effect: 'Allow'
Principal:
AWS:
- 'arn:aws:iam::${AWS::AccountId}:role/ProcurementAdmin'
Action:
- 'sts:AssumeRole'
ManagedPolicyArns:
- 'arn:aws:iam::aws:policy/AWSPrivateMarketplaceAdminFullAccess'
- 'arn:aws:iam::aws:policy/AWSMarketplaceManageSubscriptions'
- 'arn:aws:iam::aws:policy/ReadOnlyAccess'Because there is no delegation possible for Private Marketplace the organisations need to protect their Private Marketplace with SCPs. Below policy, if applied as SCP limits the possibility to manage PMP setup only to the defined role (PMP Admin) and account (Private Marketplace Account). Without this SCP any member account would be able to change PMP settings for the organisation.
{
"Effect": "Deny",
"Action": [
"aws-marketplace-management:*",
"aws-marketplace:Associate*",
"aws-marketplace:CancelChangeSet",
"aws-marketplace:Disassociate*",
"aws-marketplace:StartChangeSet",
"aws-marketplace:PutProcurement*",
"aws-marketplace:UpdateTask",
"aws-marketplace:CompleteTask"
],
"Resource": "*",
"Condition": {
"StringNotLike": {
"aws:PrincipalARN": ["arn:aws:iam::13234234234:role/PMPAdmin"]
}
}
}As mentioned earlier, organisations may also choose to limit Marketplace Purchases to a predefined role deployed to all member accounts. Granting access to this role depends on the IAM Federation setup and is outside of scope of this article, however it would be a prerequisite to successfully auditing the use. Below code snippet presents how a sample Purchasing role could be defined in terms of permissions given.
{
"Effect": "Deny",
"Action": [
"aws-marketplace:CreatePrivateMarketplaceRequests",
"aws-marketplace:Subscribe",
"aws-marketplace:Unsubscribe",
"aws-marketplace:ViewSubscriptions",
"dynamodb:PurchaseReservedCapacityOfferings",
"ec2:AcceptReserved*",
"ec2:CancelCapacity*",
"ec2:CreateCapacity*",
"ec2:CreateReserved*",
"ec2:DeleteQueuedReservedInstances",
"ec2:ModifyCapacity*",
"ec2:ModifyInstanceCapacity*",
"ec2:ModifyReserved*",
"ec2:Purchase*",
"elasticache:PurchaseReservedCacheNodesOffering",
"es:PurchaseReservedElasticsearchInstanceOffering",
"es:PurchaseReservedInstanceOffering",
"glacier:PurchaseProvisionedCapacity",
"rds:PurchaseReservedDBInstancesOffering",
"redshift:AcceptReservedNodeExchange",
"redshift:PurchaseReservedNodeOffering"
],
"Resource": "*",
"Condition": {
"StringNotLike": {
"aws:PrincipalARN": [
"arn:aws:iam::*:role/Purchasing",
"arn:aws:iam::*:role/PMPAdmin"
]
}
}
}The above limits not only the Marketplace purchases but also gives the ability to monitor purchasing of Reserved Capacity for various AWS services. In order to make the above work a organisation level restriction would be required. Below SCP limits who can buy on Marketplace to the Purchasing role defined above.
{
"Effect": "Deny",
"Action": [
"aws-marketplace:CreatePrivateMarketplaceRequests",
"aws-marketplace:Subscribe",
"aws-marketplace:Unsubscribe",
"aws-marketplace:ViewSubscriptions",
"dynamodb:PurchaseReservedCapacityOfferings",
"ec2:AcceptReservedInstancesExchangeQuote",
"ec2:CancelReservedInstancesListing",
"ec2:CreateReservedInstancesListing",
"ec2:DeleteQueuedReservedInstances",
"ec2:ModifyInstanceCapacity*",
"ec2:ModifyReserved*",
"ec2:Purchase*",
"elasticache:PurchaseReservedCacheNodesOffering",
"es:PurchaseReservedElasticsearchInstanceOffering",
"es:PurchaseReservedInstanceOffering",
"glacier:PurchaseProvisionedCapacity",
"rds:PurchaseReservedDBInstancesOffering",
"redshift:AcceptReservedNodeExchange",
"redshift:PurchaseReservedNodeOffering"
],
"Resource": "*",
"Condition": {
"StringNotLike": {
"aws:PrincipalARN": [
"arn:aws:iam::*:role/Purchasing",
"arn:aws:iam::*:role/PMPAdmin"
]
}
}
}If a organisation is more siloed in has different purchasing policies depending either on business unit, country or service line we can choose to structure the setup in a different way to also suit this requirements.
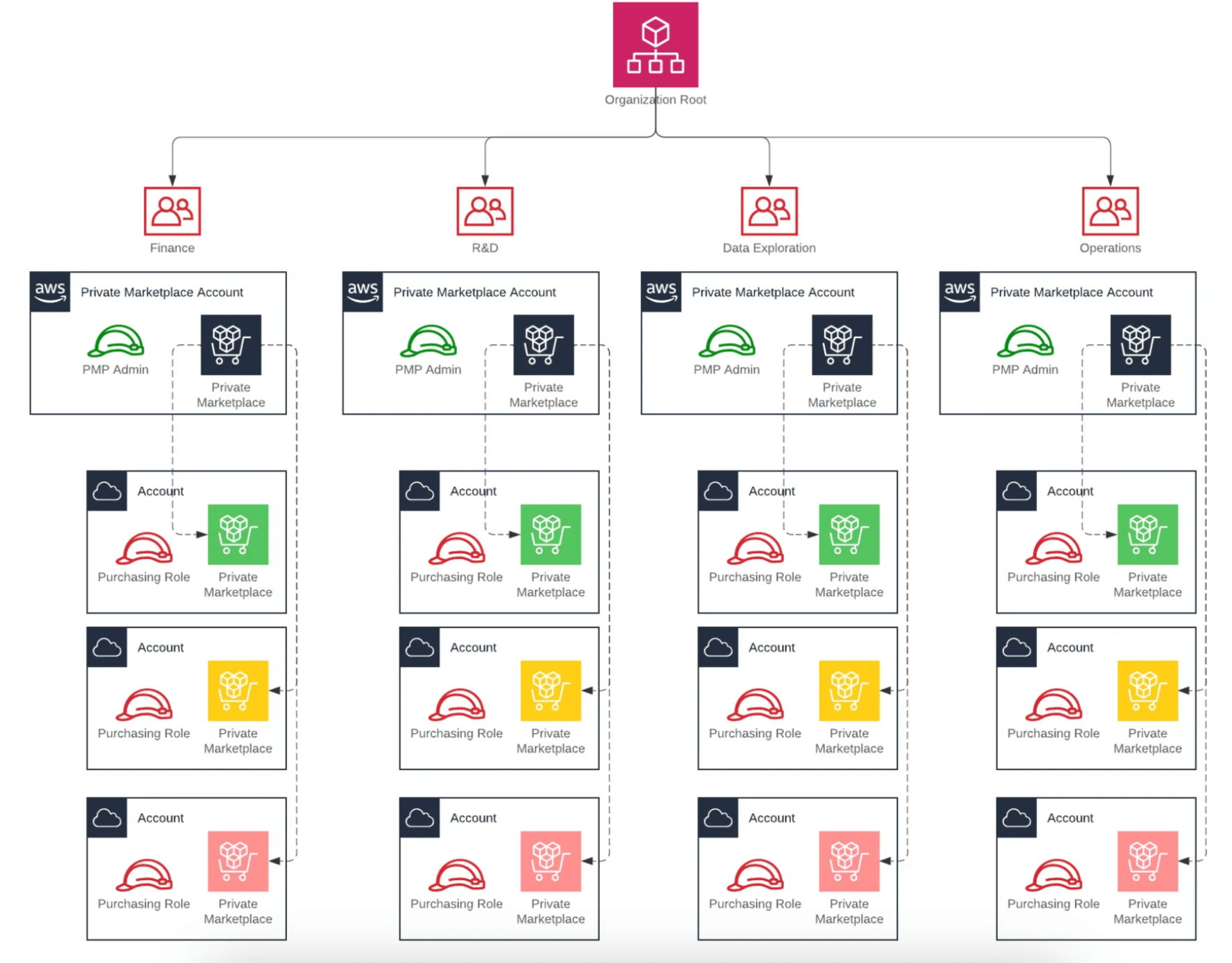
The image above shows a possible setup where there are multiple “delegated” accounts that in turn control different experiences inside of different business units. Different colours outline the possibility to further customise purchases inside a business unit if required.
Conclusion
In the ever-evolving landscape of cloud computing and data security, compliance management remains a top priority for organisations. AWS Private Marketplace offers a powerful solution to address compliance concerns by providing a controlled, centralised, and pre-approved environment for procuring and deploying AWS services. By leveraging this feature, organisations can streamline their compliance efforts, reduce the risk of violations, and enhance security across their cloud infrastructure. As businesses continue to harness the benefits of cloud computing, solutions like AWS Private Marketplace will play a pivotal role in maintaining the delicate balance between innovation and adherence to regulatory standards.
Get in Touch.
Let’s discuss how we can help with your cloud journey. Our experts are standing by to talk about your migration, modernisation, development and skills challenges.