Control your environment with Azure policy
Post • 3 min read
Building a secure environment is one of the most important aspects of the Public Cloud. Azure policy is a service that you can use to create, assign and manage policy definition whilst also easily controlling your Azure environment.
These policy definitions can be used to enforce a desirable state of newly created services or to audit current infrastructure. You can use built-in policies or create using JSON syntax to create new policy appropriate to the requirements.
With Azure policies you can achieve results:
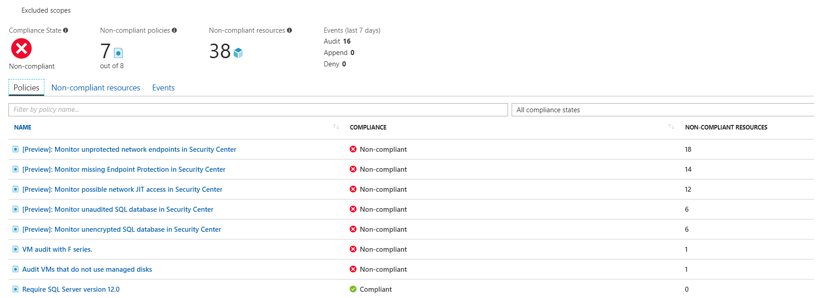 Initiative Compliance
For using compliance evaluation standard price tiers are required.
The Azure Policy services are currently in the preview state. This is a service that will most likely be constantly developed, but it could be one of the important services ensuring security in the public cloud environment, making it definitely worth some attention.
Initiative Compliance
For using compliance evaluation standard price tiers are required.
The Azure Policy services are currently in the preview state. This is a service that will most likely be constantly developed, but it could be one of the important services ensuring security in the public cloud environment, making it definitely worth some attention.
- Audit
- Deny
- Append
- AuditifNotExists
- DeployifNotExists
The above example protects the environment before creating a network card without an assigned Network Security Group. To create policy definition you can choose:{"policyRule": {"if": {"allOf": [{"field": "type","equals": "Microsoft.Network/networkInterfaces"},{"not": {"field": "Microsoft.Network/networkInterfaces/networkSecurityGroup.id","equals": "[parameters('nsgId')]"}}]},"then": {"effect": "deny"}},"parameters": {"nsgId": {"type": "String","metadata": {"displayName": "Network Security Group Id","description": "Resource Id of the Network Security Group","strongType": "networksecuritygroup"}}},"metadata": {"category": "LabCategorySecurity"}}
- Azure portal
- Powershell
- Azure CLI
- REST API
 Initiative Compliance
For using compliance evaluation standard price tiers are required.
The Azure Policy services are currently in the preview state. This is a service that will most likely be constantly developed, but it could be one of the important services ensuring security in the public cloud environment, making it definitely worth some attention.
Initiative Compliance
For using compliance evaluation standard price tiers are required.
The Azure Policy services are currently in the preview state. This is a service that will most likely be constantly developed, but it could be one of the important services ensuring security in the public cloud environment, making it definitely worth some attention. Get in Touch.
Let’s discuss how we can help with your cloud journey. Our experts are standing by to talk about your migration, modernisation, development and skills challenges.

Ilja’s passion and tech knowledge help customers transform how they manage infrastructure and develop apps in cloud.
Ilja Summala
LinkedIn
Group CTO